
Rethinking Chemical Security Risks
There is a need for a value-driven security risk assessment in chemical clusters.
Chemical plants are basically attributed with large inventories of hazardous materials whose accidental or intentional release could result in catastrophic events. The proximity of chemical plants to residential areas and transportation networks, specifically in industrialized and densely populated European countries such as Belgium, Germany, France, and The Netherlands, makes the consequences of such undesired releases even more catastrophic. Finally, the ever-increasing complexity and interdependencies in the chemical industry, particularly with the emergence of chemical industrial parks (chemical clusters) that incorporate a number of chemical plants within a tight neighborhood (e.g., Port of Rotterdam in The Netherlands), exacerbate the severity and the extent of potential consequences, e.g., via domino effects.
As opposed to safety issues in chemical plants, which can be a matter of random failures, human errors, negligence, or natural hazards, security issues such as terrorist attacks are caused by deliberate actions of human agents with the possible intention of creating maximum damages. Compared to long-established regulations and state-of-the-art techniques in safety risk assessment of hazardous industries, the importance of security risk assessment was drawn into attention mainly after the 9/11 terrorist attacks in the United States. Nevertheless, according to a survey conducted in Belgium, in chemical companies the likelihood of extreme security issues such as terrorist attacks has been deemed very low. The relatively recent security issues in two chemical plants in France in June 2015 and July 2015 have, however, exposed the vulnerability and attractiveness of chemical plants as potential targets for such intentional acts. These attacks raised the chemical industry’s awareness of imminent terrorist attacks and the need for taking effective measures, not only to reduce the attractiveness and vulnerability of chemical plants but also to reduce the potential consequences of successful attacks.
Security Risk Assessment Methods
For assessing security risks, the chemical industry needs methods that take into account that chemical plants are increasingly part of clusters of such plants and that incorporate the moral, societal, and economic aspects of security policies.
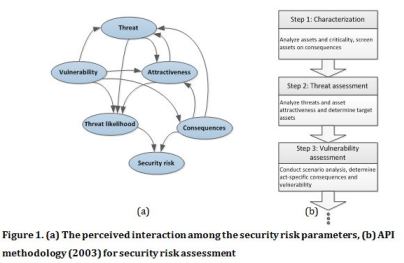
The likelihood of a successful attack is an intertwined function of the type of threats, possible attack scenarios, the vulnerability and the attractiveness of chemical plants, and the effectiveness of the security countermeasures (Figure 1(a)). However, mainly inspired by the security vulnerability assessment guidelines set forth by, among others, the American Petroleum Institute (API, 2003), the majority of the developed techniques follow a linear approach to security risk assessment (e.g., sequential scoring of threat, attractiveness, vulnerability, etc.) (Figure 1(b)). However, such linear approaches all short to taking into account the complex interdependencies prevailing in chemical clusters. These shortcomings hinder the application of traditional risk assessment methodologies to chemical clusters where a number of chemical plants are technically, operatively, strategically, or managerially dependent on one another. Furthermore, a majority of the developed security risk assessment methodologies are static in nature, only representing a snapshot of a security issue. As a result, they are not capable of taking new information (also known as precursors) into account to update the security risks and adjust the security management strategies accordingly.
Society demands, moreover, a more moral sensitivity of industry in its policies to mitigate risks, that, as can be argued, will improve rather than frustrate traditional risk assessments that focus on only a rational (technical) idea of the risks.
A Proposed Conceptual Framework
For addressing the aforementioned drawbacks in security risk assessment of chemical clusters, we propose a framework (Figure 2) comprising ethical (α), technical (β), and economic (γ) aspects of security risk in chemical clusters with a particular emphasis on interdependencies, stakeholders, and societal values. First, moral, technical, and economic risk parameters need to be identified and processed. In Part 2, the risks will be calculated in a dynamic way, regarding both the single plants and the chemical cluster. In Part 3, the outcomes of the risk analysis will be used, in conjunction with moral and economic aspects and constraints, to set security management policies and enable security-informed decision making.
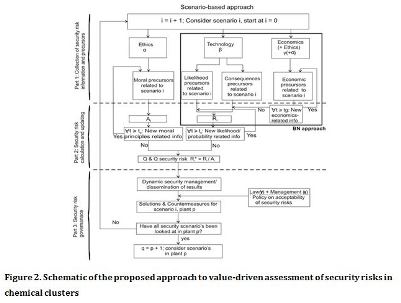
To develop the methodology, a number of steps need to be taken in accordance with the interdisciplinary nature of security risk in chemical plants.
Ethical Aspects of Security Risk
In addition to objective probabilities and consequences of security events, moral analysis should play a key role in the calculation of security risks. Traditional risk assessment mainly serves the purpose of having a rational (technical) idea of the risks. However, in order to gain a more realistic measure of risks, not only the technical aspects but also the moral aspects of risk should be taken into account. The moral aspects will be used to modify the concept of conventional risk toward a "value-driven" risk, with three envisaged advantages:
First, the inclusion of moral aspects in the security assessment will probably result in fewer debated outcomes, ensuring the company’s policy is driven neither by pure rationale nor by pure emotion, but by a combination of both, and thus being more responsible to all stakeholders.
Second, the application of "value-driven" security risk can benefit the vulnerability analysis. Conventional risk analysis provides a basis for the identification of technical vulnerabilities. However, the mindset of the public (and also terrorists) toward vulnerabilities can be quite different, leading to the concept of emotional vulnerability. The fact that an adversary who aims to intentionally cause damage to chemical plants may be a layperson and thus bases his decision and course of action on laypersons' perception of vulnerability necessitates the inclusion of moral aspects in the security risk assessment.
Third, a company's policy focused on security only is bound to clash with other moral values, such as safety, leading to moral overload or moral conflicts in such policy. For instance, for improving safety, the European Council Directive (Seveso III) on the prevention of major accidents mandates that chemical plants provide information on the type, the inventory, and the location of the hazardous materials in the plant, the preventive measures in place, and possible accident scenarios. A security policy may now want to again conceal such information so it does not fall into the hands of adversaries. Security measures should not conflict, however, with earlier demands by society on the chemical industry to become more transparent about safety risks, calling for the development of company policies that realize both security and safety.
Technical Aspects of Security Risk
To develop an integrated methodology, the influential parameters such as threats, vulnerabilities, attractiveness, attack scenarios, and the extent and severity of consequences should be investigated. A particular emphasis should be given to the interdependencies that can ramp up the likelihood of successful attacks or can exacerbate the severity of consequences via, for example, domino effects.
In order to account for uncertainties and interdependencies, and also to facilitate the incorporation of precursor data in risk assessment and updating, applicability of probabilistic techniques such as Bayesian network (BN) can be examined. Owing to their flexible graphical structure and the robust probabilistic engine, BN has widely been applied to safety assessment of chemical facilities, but its application to security risk assessment has been very limited.
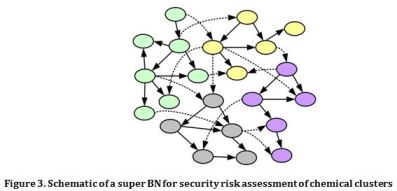
Considering the interdependencies among chemical plants within a chemical cluster, a BN can be developed for the entire cluster (Figure 3) where the nodes with identical color belong to the same chemical plant. Solid arcs and dashed arcs denote, respectively, the dependencies within individual chemical plants and the chemical cluster. The BN can be used for an integrated security assessment and management, taking into account both security and safety precursors so as to assess and update the security risks in a dynamic fashion.
Economic Aspects of Security Risk
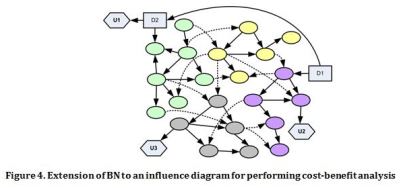
To make security risks tangible, the consequences should be interpreted in economic terms. Prevention costs and avoided accident costs are used in an economic assessment to translate rational risks into economic terms. Direct costs (human casualties, property damage, etc.), as well as indirect costs (loss of business continuity, damage to company reputation and ensuing drop in stock market, etc.), should be considered. Having the risks in monetary unit along with the cost and effectiveness of relevant countermeasures, a cost-benefit analysis can be performed to determine the optimal allocation of collective resources (chemical cluster wise) in order to reduce the risks as low as reasonably practicable. To this end, the super BN depicted in Figure 4 can be extended to an influence diagram by adding decision and utility nodes (Figure 4). The developed influence diagram can be employed for a wide variety of decision analyses, including cost-benefit analysis.
This article originally appeared in the September 2017 issue of Occupational Health & Safety.